Secure Your MCP Ecosystem.Complete visibility & runtime protection for AI agents
Without proper controls, attackers can exploit MCPs to bypass standard protections barriers.
Trusted By

MCP Servers Create Security Risks
MCP Security Risks
Remote Code Execution
Malicious prompts or tools can trigger unauthorized execution, compromising your entire system and exposing sensitive infrastructure
Rogue Servers & Tool Misuse
Attackers can abuse or impersonate MCP servers, deploying unauthorized tools that bypass security controls
Client Impersonation
Fake clients can steal sensitive data by impersonating legitimate services and accessing protected resources
Wallarm MCP Security
Complete MCP Visibility
Discover all MCP servers and tools across environments. Identify vulnerabilities, non-compliant tools, and rogue servers instantly
MCP Runtime Protection
Apply granular security controls to specific tools and servers. Detect business logic abuse with AI-powered analysis
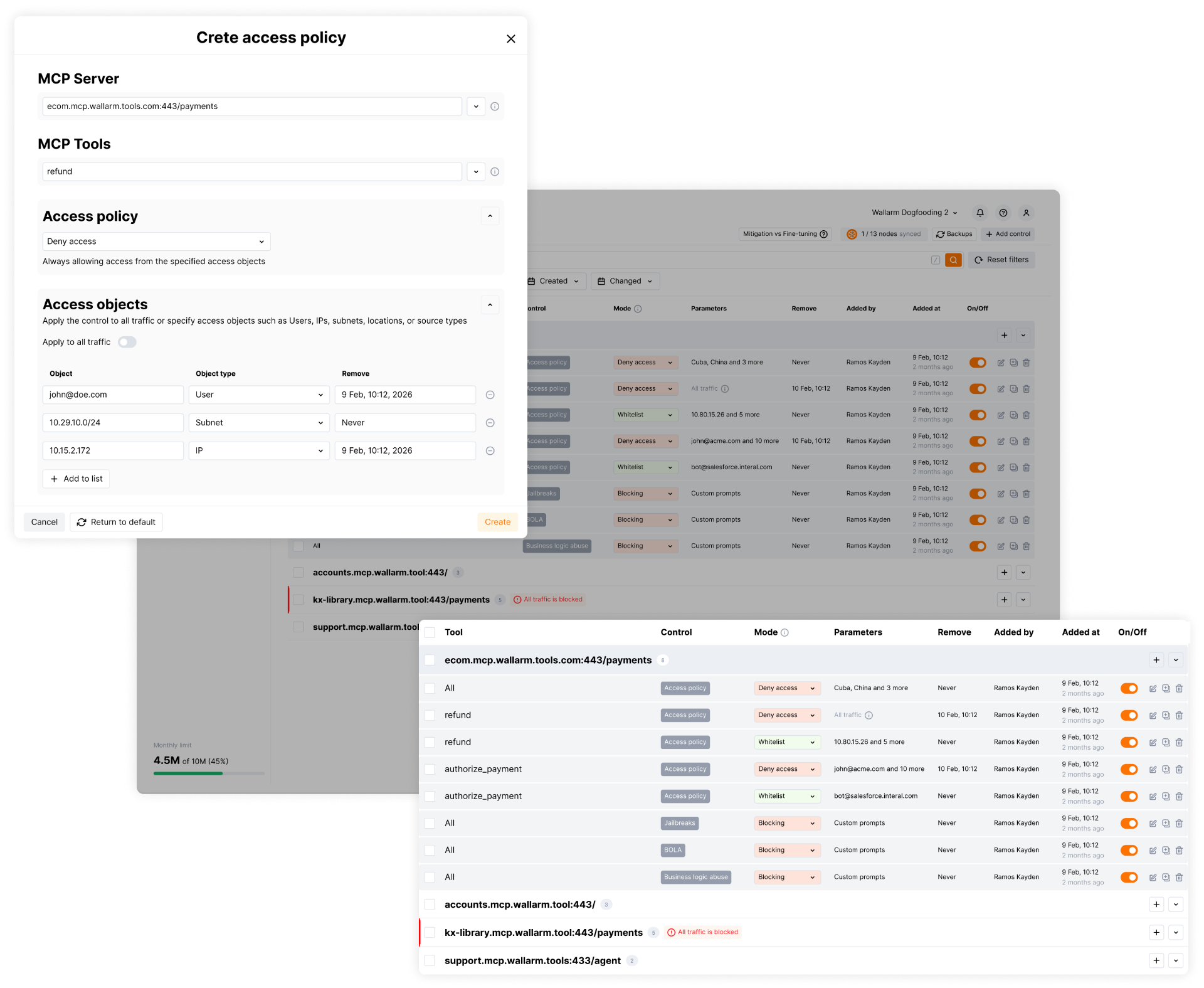
Granular Access Policies
Set precise access controls by user, IP, subnet, and traffic source. Whitelist trusted bots and block vulnerable tools instantly
Wallarm Approach to MCP Visibility
Gain complete visibility into your MCP ecosystem with automatic discovery and continuous monitoring of all servers, tools, and agent interactions.
Automatic MCP Discovery
Automatically identify all MCP servers, tools, and prompts across your entire infrastructure without manual configuration
Real-Time Tool Inventory
Maintain a live inventory of all MCP tools, their capabilities, permissions, and usage patterns across environments
Vulnerability Detection
Identify vulnerable, outdated, or non-compliant MCP tools and servers before they can be exploited
Dependency Mapping
Visualize relationships between agents, servers, and tools to understand your MCP ecosystem's complete attack surface
Wallarm Approach to MCP Runtime Protection
Protect your MCP servers in real-time with AI-powered threat detection and granular access controls that stop attacks without slowing down your agents.
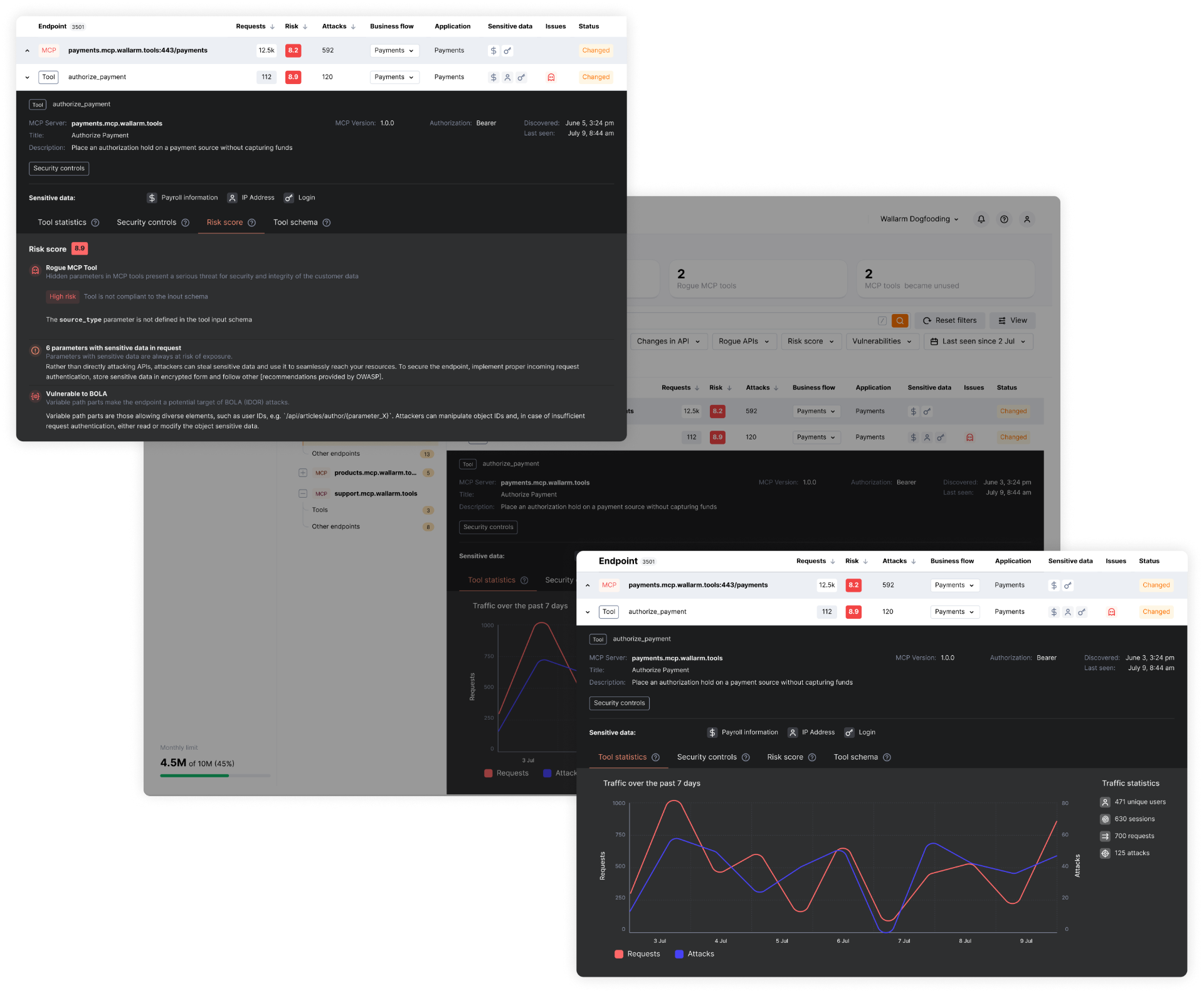
Real-Time Threat Detection
AI-powered analysis detects and blocks malicious prompts, unauthorized tool calls, and business logic abuse as they happen
Granular Access Policies
Define precise access controls by user, IP, subnet, and traffic source. Whitelist trusted agents and block risky tools instantly
Automated Response
Automatically quarantine rogue servers, revoke compromised credentials, and isolate suspicious agent behavior
Data Loss Prevention
Prevent sensitive data exposure through MCP prompts and responses with intelligent content filtering and redaction
"We didn't need to change anything in the application deployment infrastructure. The installation itself is easy and straightforward."
Konstantin Golubitsky
CTO

